The Anatomy of a Phishing Email – How to Spot the Red Flags
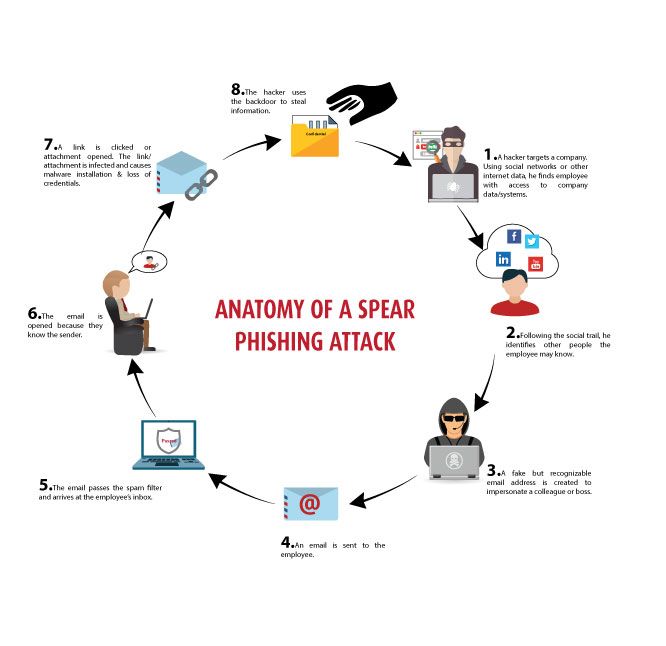
Phishing is one of the most prevalent and effective cyber threats in the world today. It’s easy to fall victim to a cleverly crafted phishing email that impersonates trusted organizations. But understanding how to recognize the signs can protect you and your business from financial loss, data breaches, and system compromises. In this blog post, we will break down the anatomy of a phishing email and teach you how to spot the red flags before it’s too late.
1. What is Phishing?
Phishing is a form of cyber attack where attackers impersonate legitimate institutions (banks, government agencies, or trusted companies) to trick individuals into sharing sensitive information such as usernames, passwords, and financial data. Phishing attacks are often carried out through email, though they can occur through text messages (SMS phishing) or social media (social engineering).
2. Common Elements of a Phishing Email
Here’s what you need to look for in a typical phishing email:
-
Suspicious Sender Address: Phishing emails often come from email addresses that look legitimate at first glance but have slight misspellings or unusual domain names. For example, a legitimate email from your bank may come from [email protected], while a phishing email might use [email protected].
-
Urgent, Fear-Inducing Language: Phishers want to provoke an emotional reaction. Look for phrases like “Immediate action required,” “Your account has been compromised,” or “Suspicious activity detected.” These scare tactics aim to get you to act quickly without thinking.
-
Unusual Links: A phishing email often contains a link that seems like it’s directing you to a trusted website, but if you hover over it, the URL will look suspicious or contain extra characters. Never click on links until you’re sure they’re safe.
-
Spelling and Grammar Mistakes: A legitimate company will generally proofread their communications. Look for glaring grammar or spelling mistakes as a strong indicator of phishing.
-
Unsolicited Attachments: Be wary of any email attachment from an unknown sender. Even attachments from seemingly trusted sources can be a vector for malware.
3. How to Protect Yourself from Phishing
-
Double-Check the Source: Always verify the sender’s email address before clicking on links or opening attachments. Contact the institution directly using verified contact details (e.g., phone number or official website).
-
Use Anti-Phishing Software: Most security software now includes anti-phishing protection that alerts you when you’re visiting a potentially malicious website.
-
Implement Multi-Factor Authentication (MFA): Even if your credentials are compromised through phishing, MFA can help stop attackers from gaining full access to your account.
-
Educate Your Team: Employees are the first line of defense against phishing. Conduct regular training to help them recognize and report suspicious emails.
4. What to Do if You Fall for a Phishing Attack
If you click on a phishing link or share sensitive data, take immediate action:
-
Change your passwords.
-
Notify your IT department if it’s a company-related account.
-
Report the phishing email to the legitimate institution being impersonated.
Phishing attacks are increasingly sophisticated, but knowing how to spot the signs can drastically reduce your risk of falling victim to them. Always stay vigilant and don’t let attackers trick you into compromising your data.